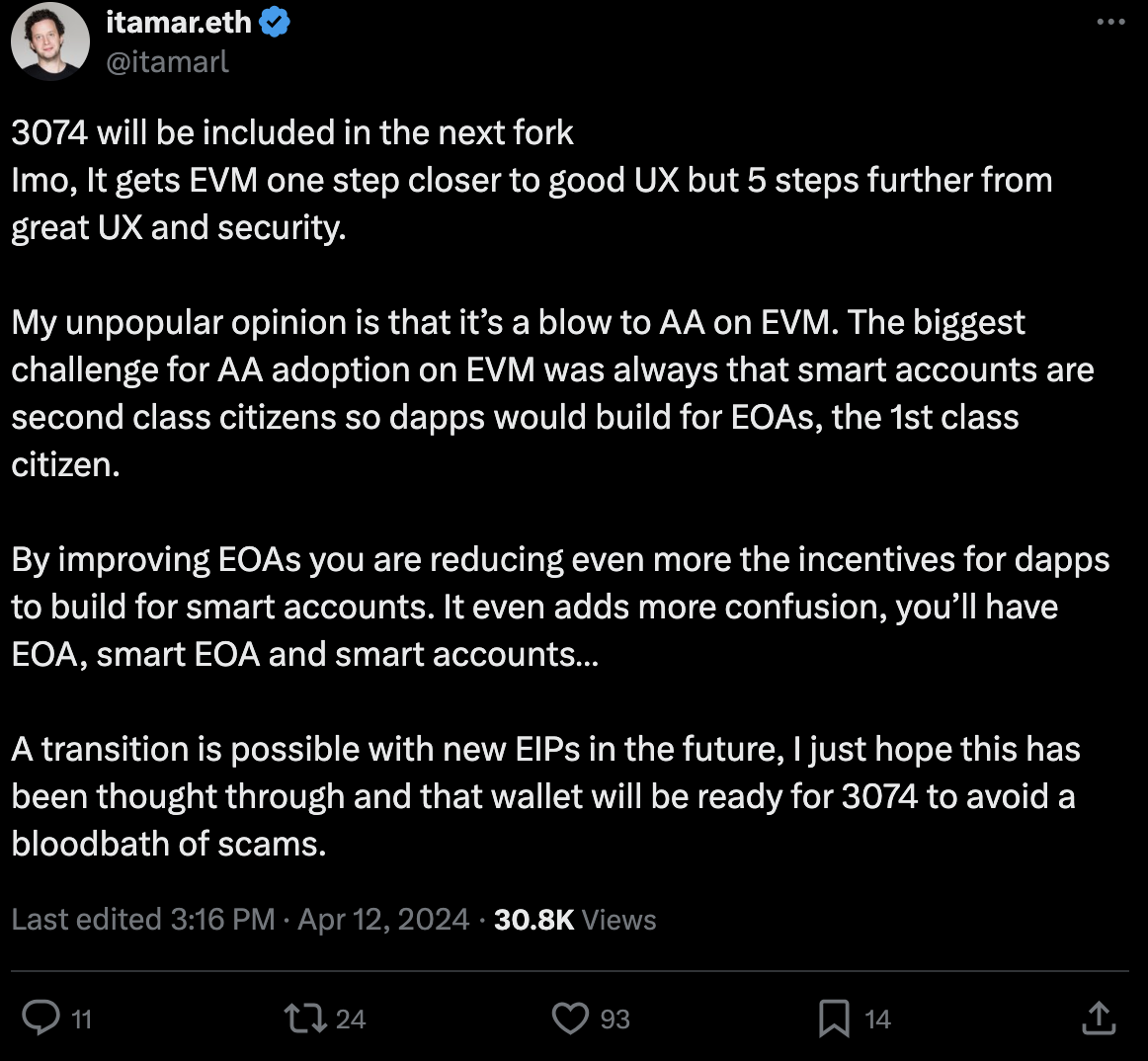
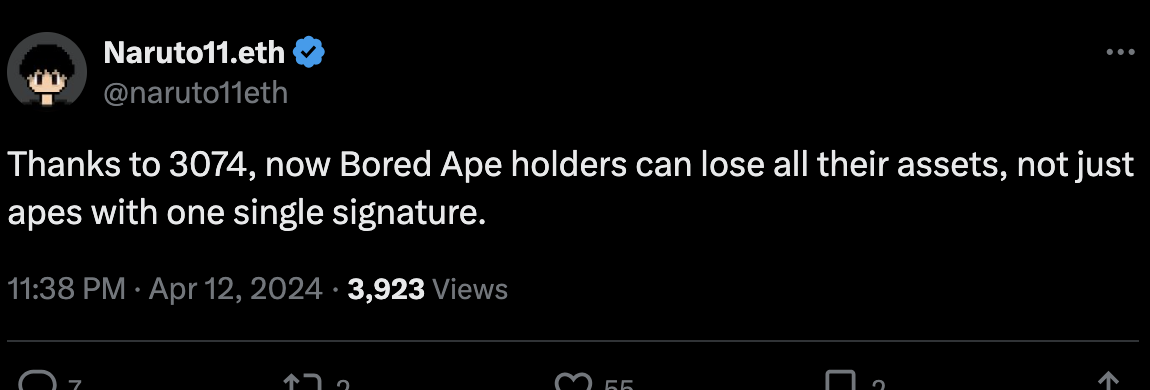
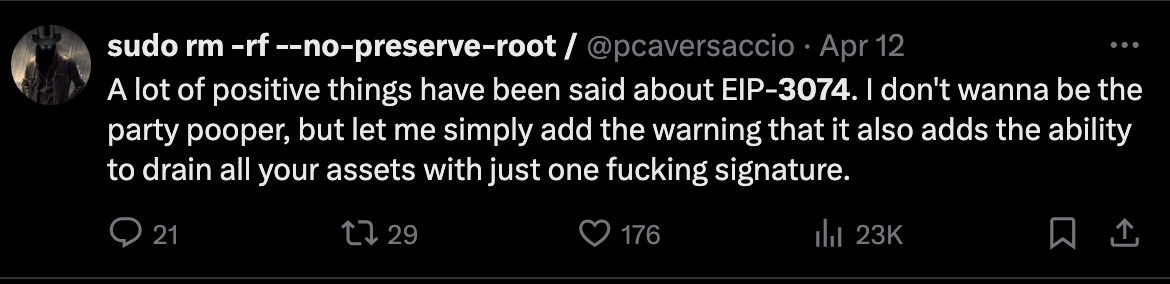
There have been mountains of text written on this forum and elsewhere about EIP 3074, but getting to the signal through the noise can be hard. Here’s a short summary of why EIP 3074 is a bad idea:
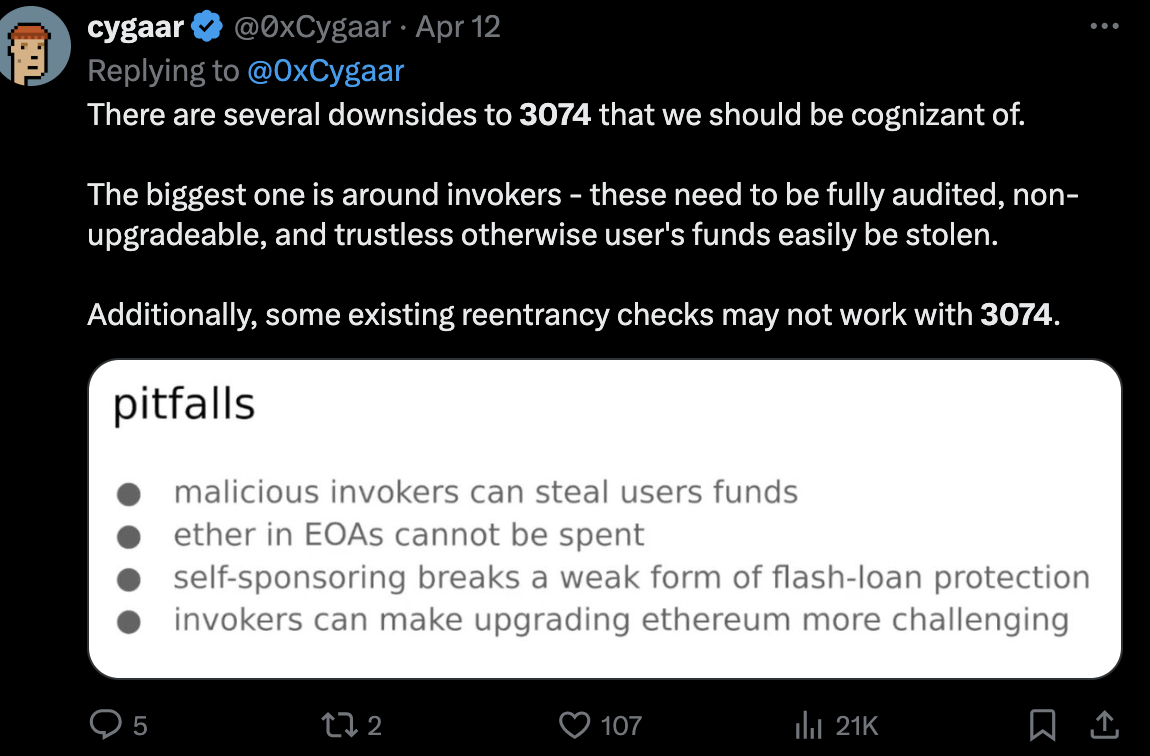
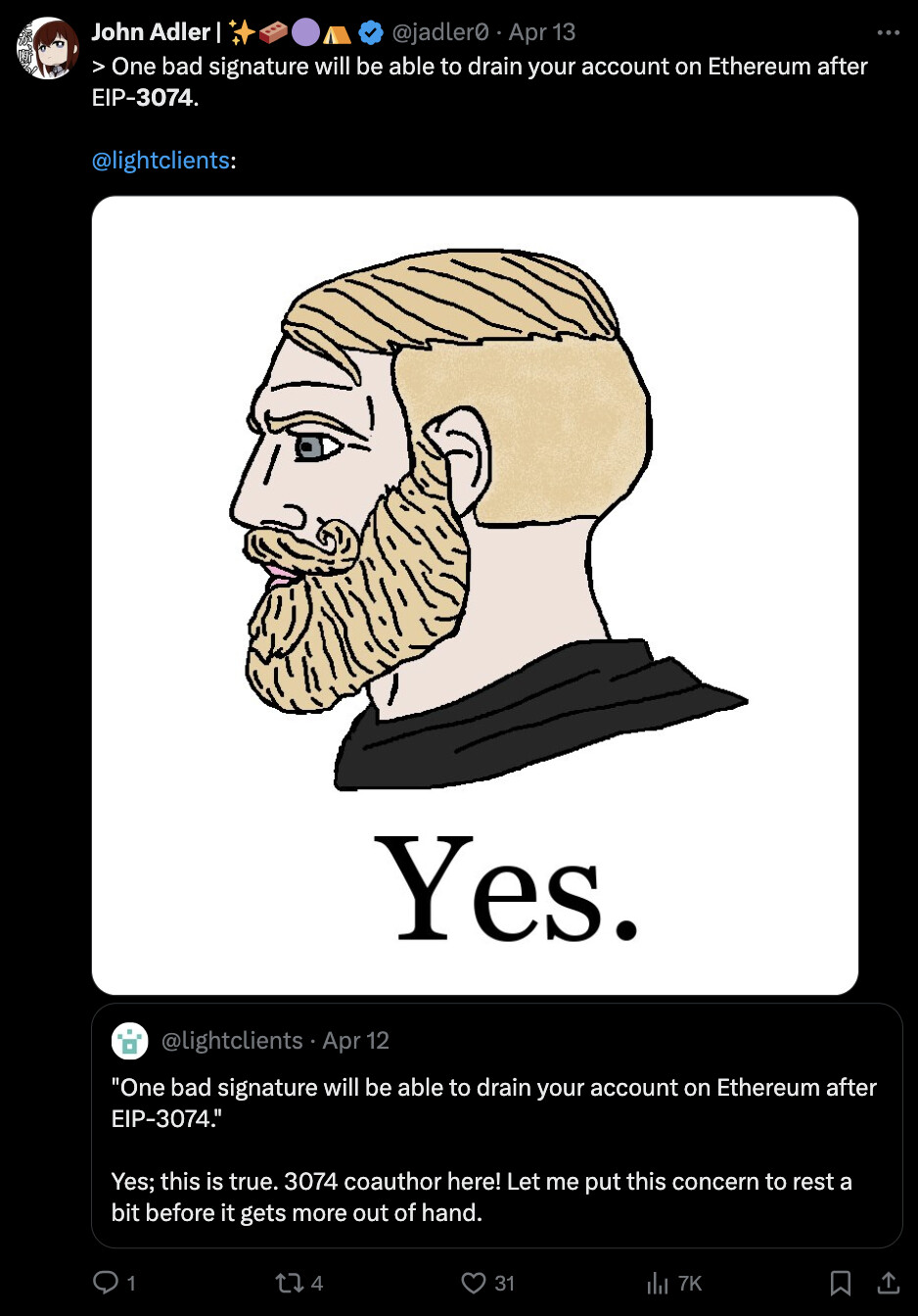
- User funds at risk: One signature and you lose everything. Relies on wallets preventing this, and users understanding the new security model. Fragile assumptions. Hardware wallets won’t protect users unless their UX is rehauled
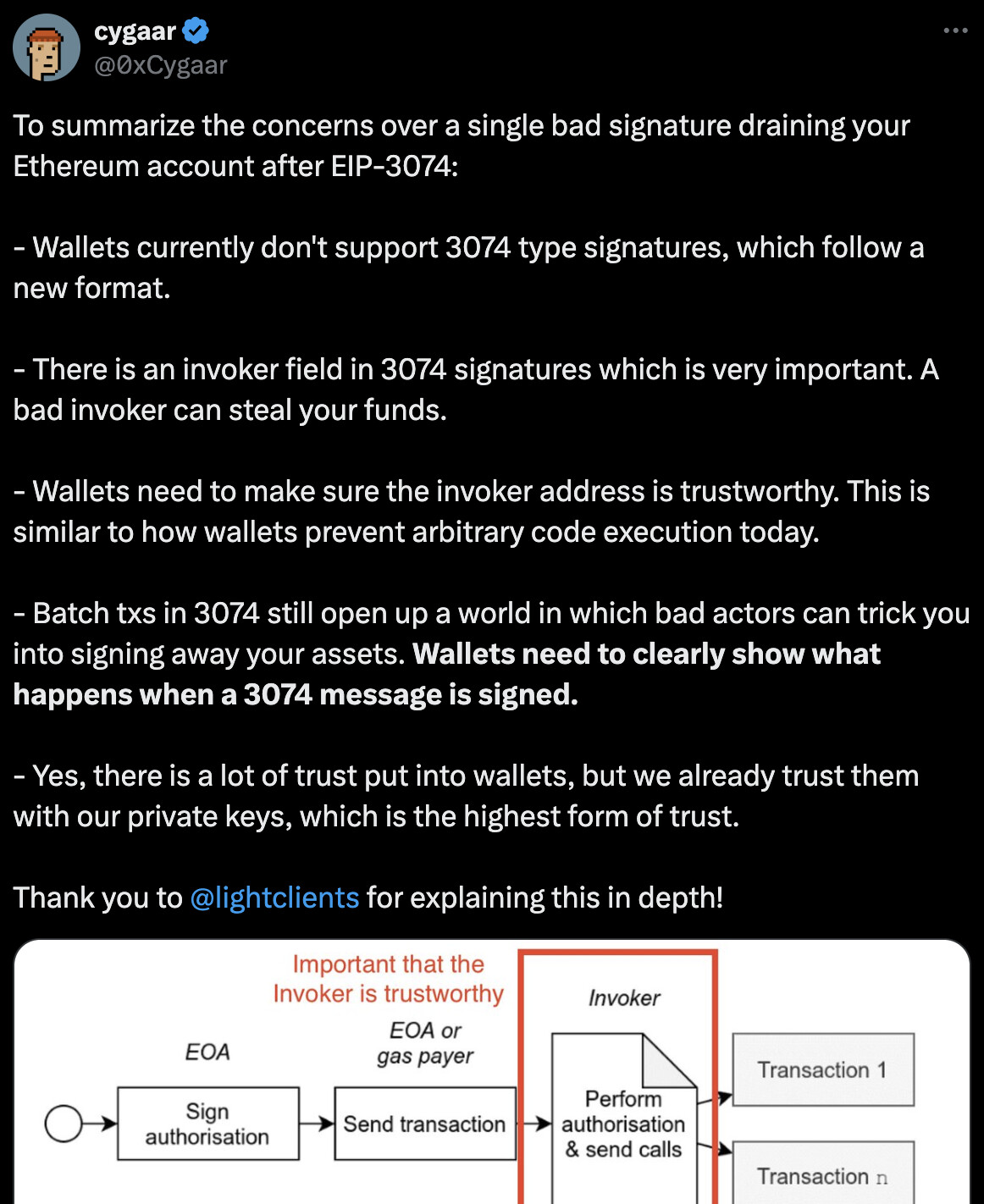
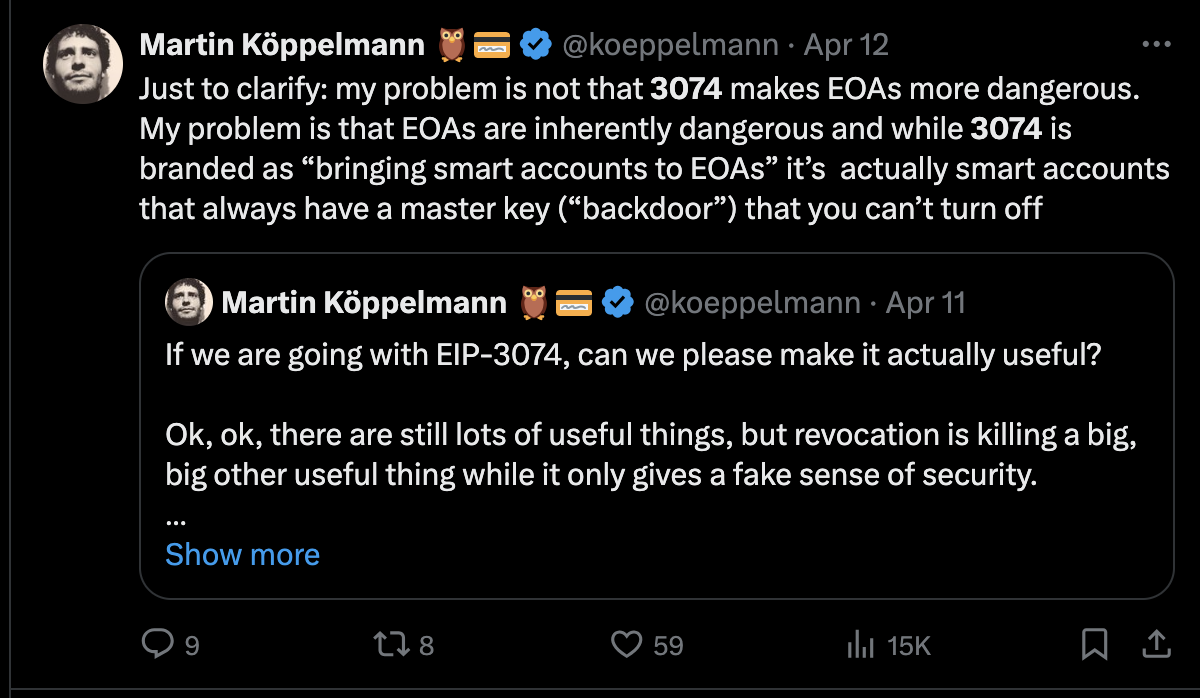
- Dangerous lack of security controls: to enable use cases such as gas abstraction EIP 3074 requires giving full access to all of your assets. EIP 3074 is trust maximized. It is an all or nothing “sudo root” access model. This is unlike 4337’s trust minimized design where paymasters are incapable of stealing your funds
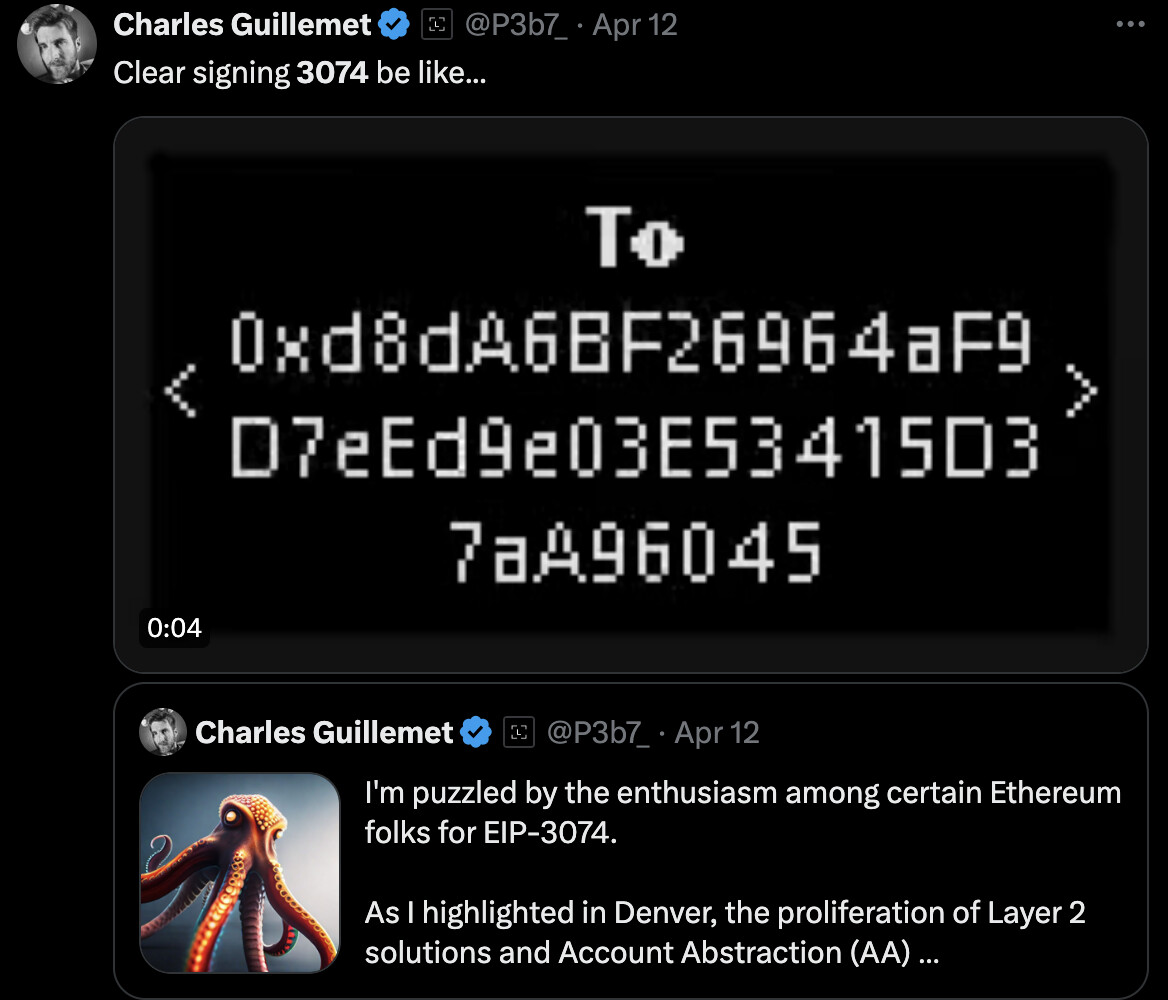
- Confusing security model that’s harder for users to understand: EIP 3074 makes the EOA security model much harder to understand, even for experts, but especially for normal humans. Violates the principle of least surprise (see more below)
- Doesn’t improve UX overall: because losing all of your funds to a scam is not good UX. The benefits EIP 3074 claims to provide can be achieved more safely in other ways
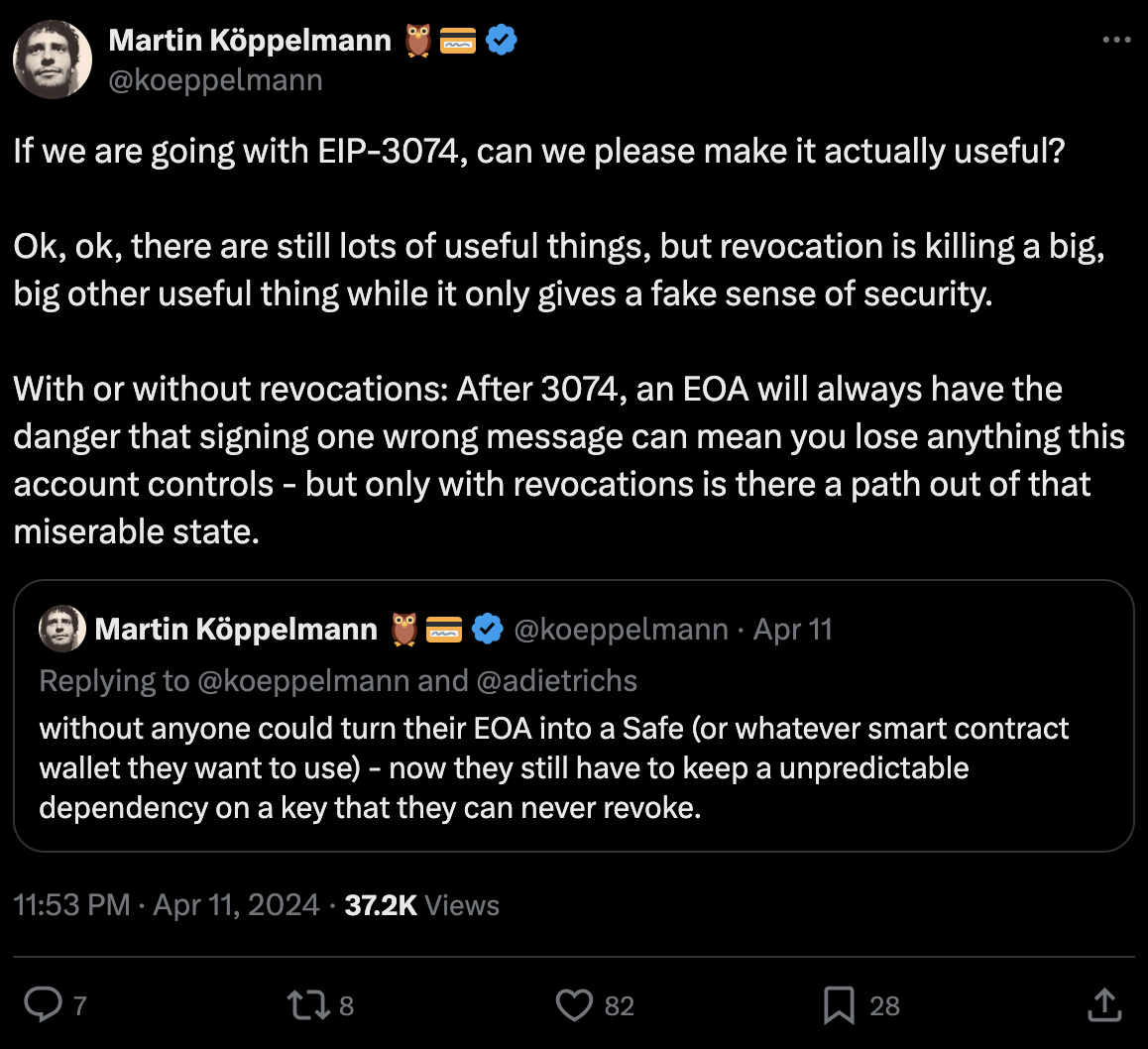
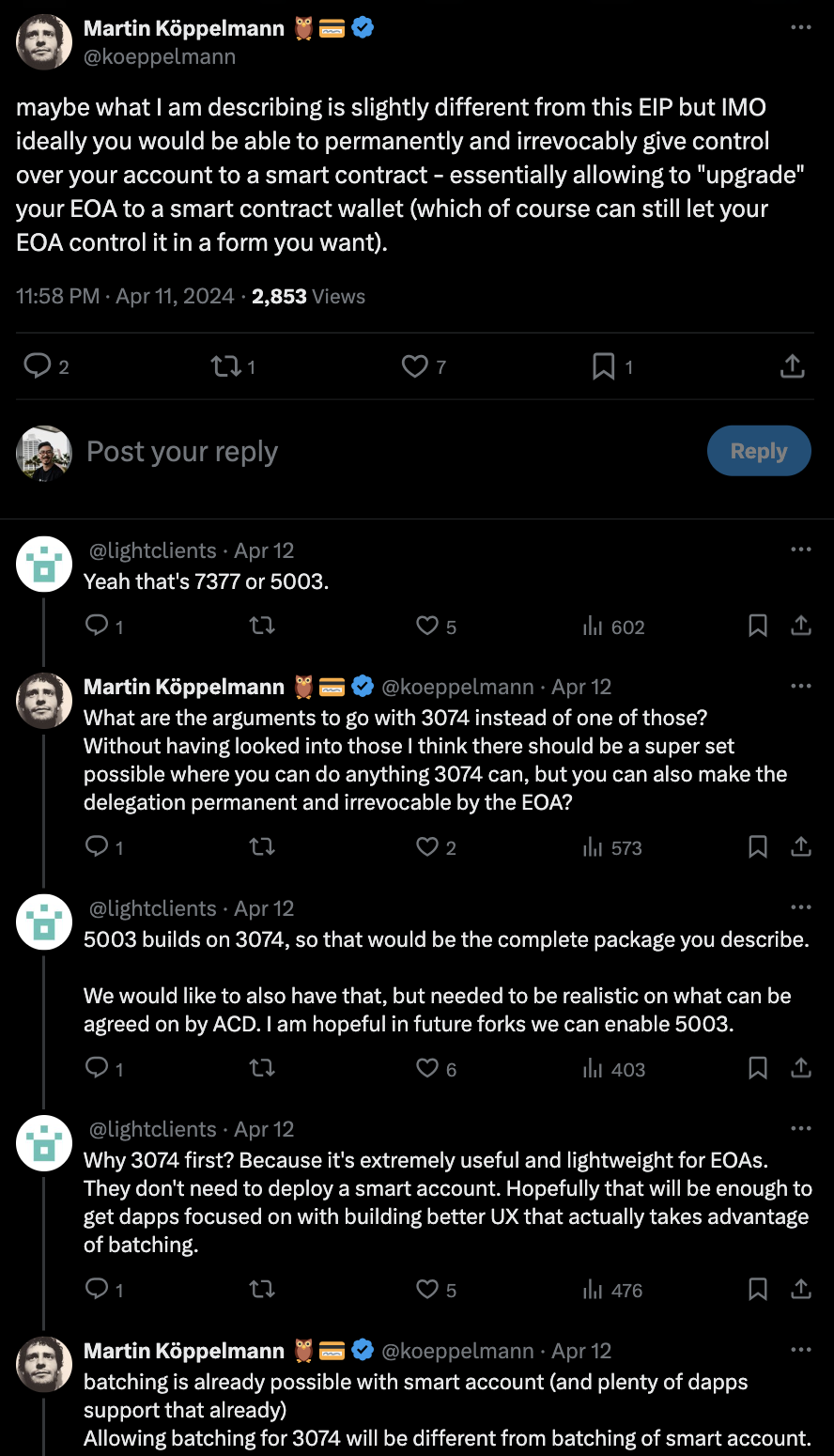
- Other security problems: adds new authorization methods to an EOA while being incapable of revoking the old hardwired EOA key. Many potential problems with breaking dapp assumptions around EOAs. Needs more thorough auditing
- Permissioned innovation: dapp devs won’t be able to develop their own invokers since all wallets will whitelist them once users start getting scammed.
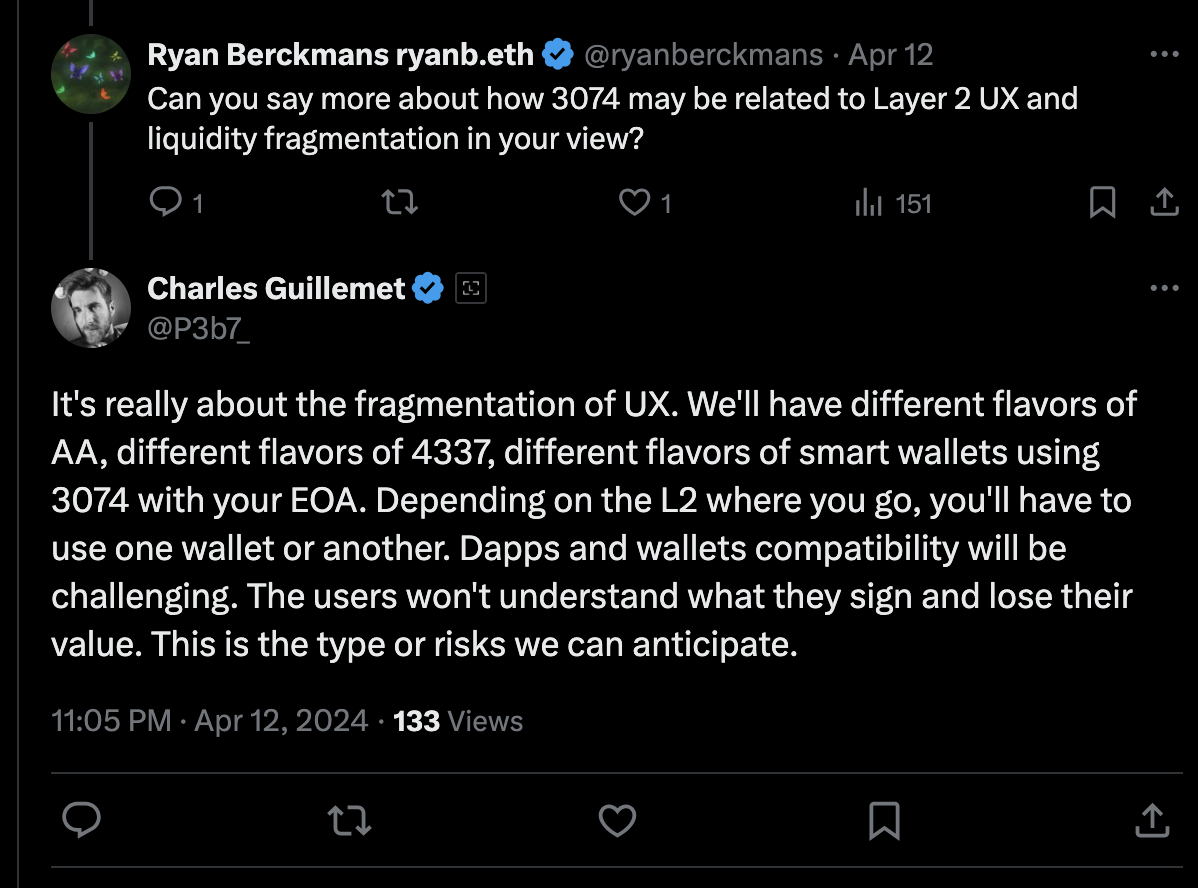
- Creates two incompatible wallet stacks: This will fragment UX and liquidity even more
- Unnecessary: given that account abstraction (ERC 4337) is already on mainnet and we are on the way to having gas efficient native account abstraction in the protocol and standardized on all the rollups
- Enshrines friction and bloat: Instead of helping us on the path to account abstraction, EIP 3074 enshrines EOAs and adds an ugly layer of cruft to the protocol that we will never be able to get rid of. As soon as it gets in, the campaign for more kludgy EIPs built on top of it will start. Patches to patches to patches, all the way down.
- Incompatible with inclusion lists: which we need to mitigate how easy it is now to censor transactions now with centralized block building
- Strategically bad second order effects: promotes centralized solutions as the path of least resistance (eg centralized meta transaction relays, too big to fail monopoly around Metamask’s invoker contract)
- Credit for these arguments goes to various critics of EIP 3074 including:
- Vitalik: “we should be moving beyond EOAs not enshrining them”
- Yoav Weiss, EF security fellow and architect of 4337: “ERC 4337 vs EIP 3074”
- Ansgar @ EF researcher: one of the original EIP 3074 authors
- Charles Guillemet, CTO at Ledger
- Martin Köppelmann Gnosis co-founder
- Itamar Lesuisse: Founder and CEO of the Argent wallet
- Patricio @ Founder at POAP
Why is it a problem that EIP 3074 violates the principle of least surprise?
The general problem with losing the principle of least surprise is that the user expects a transaction to happen once, now. With 3074 it becomes “the transaction may happen any number of times now or in the future unless the invoker enforces replay protection”.
In addition there’s the issue of opaqueness (unlike a batching transaction type). From looking at the transaction, it’s impossible to know exactly what it’s going to do. Maybe the invoker transfers the tokens as you requested but also sets an allowance for someone to withdraw more in the future. Or maybe it sponsors your gas for some transaction but also delegates your governance tokens in some project to a malicious delegate who will silently collect a lot of voting power by sponsoring people’s transaction in some other protocol.
Users won’t notice since they retain their tokens. They just delegated their voting power to an attacker but are not affected directly. Or maybe an invoker is an upgradable proxy that is safe now, but in the future it’ll change its implementation to do something else and reuse your old AUTH. Easy to come up with scary scenarios.