Thanks for talking through the design with me on this @strollinghome! Here are the main pieces of feedback we had while working on support for the draft version at OpenSea.
EIP 1271 Support
We discussed this one, but wanted to repeat it here. In order to support validating 1271 signatures, we needed the creator address added to the log. Thanks for including that! This will allow support for SCW and multi-sig creators.
Note for anyone else implementing verification that you can’t just ecrecover and use that address directly, since it may be an EOA signing for a different address using 1271.
712 Payload / Phishing
The 712 payload included in the spec confused me & I believe might enable an abuse vector.
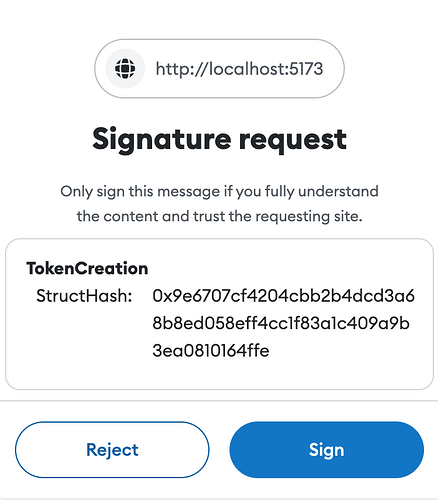
From the spec:
Creator consent is given by signing an EIP-712 compatible message; all signatures compliant with this EIP MUST include all fields defined. The struct signed is:
struct TokenCreation {
bytes32 structHash;
}
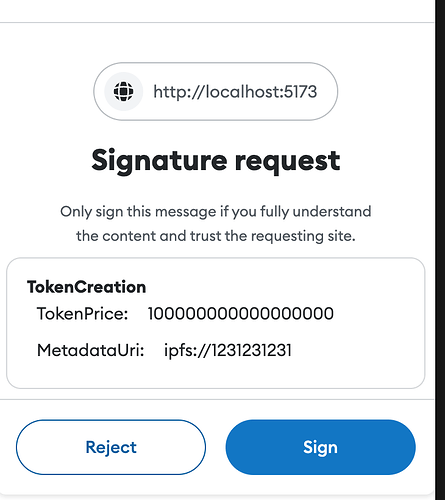
Reading that, I was expecting the primary type of the 712 payload to be TokenCreation with an included structHash. I think what is intended (as written) is for the structHash to replace hashStruct(message) from the 712 spec, allowing any arbitrary 712 message payload. From the comments above, it looks like this was changed to allow flexibility in the payload for factory contracts.
The issue I see is that this enables contracts to present any signature on the verifying domain (e.g. sign in messages) as a creatorship attestation. This will make phishing these signatures much easier since the user signing them won’t be able to tell what the signature is being used for.
A specific and explicit 712 signature for a creatorship attestation would make this more robust and less prone to abuse. Factory contracts could still support this by prompting the user to sign the specific creator attestation, and then including that signature in the (potentially also signed) payload for the contract creation.