Lists of developers that are in support here and here.
Mark Tyneway from Optimism as well as Arbitrum (posted above, also consulted DZack23 on twitter) are in support.
If you don’t consider the developers that are writing the code responsible for the majority of the Ethereum chain usage ‘unanimous’, I don’t know what to tell you. If you haven’t seen these lists before, then that’s exactly my point about joining the discussion late.
I’m pointing out that if you are saying it’s a question of tradeoffs, you should give more weight to user feedback
I am asking you to get up to speed privately and then post examples and specific feedback, rather than general concerns. I have responded to every single point in @ekpyron’s post as well as @ethchris’s, that’s pretty far from gatekeeping the discussion I think. An open discussion is not the same as an open and productive discussion.
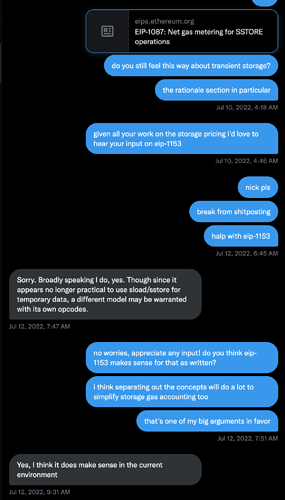
From Nick in July 2022.
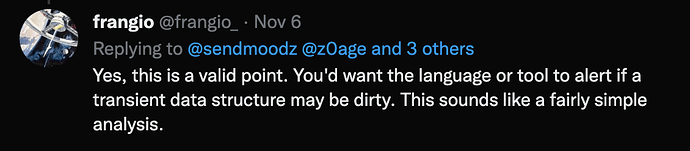
From @frangio about static analysis https://twitter.com/frangio_/status/1589372426135011329
I will seek more out. Anyone in particular you want to hear from?